Ataques de repetição no WordPress: ameaça real ou mito exagerado?

Let’s clear something up first.
Replay attacks don’t look scary.
They don’t smash passwords.
They don’t inject evil code with green hacker text flying everywhere.
They’re sneaky. Polite. And annoyingly effective.
And yes—they absolutely apply to WordPress sites.
Especially if your site handles logins, payments, contact forms, AJAX requests, or anything involving “Submit” buttons.
So… What Is a Replay Attack (In Human Language)?
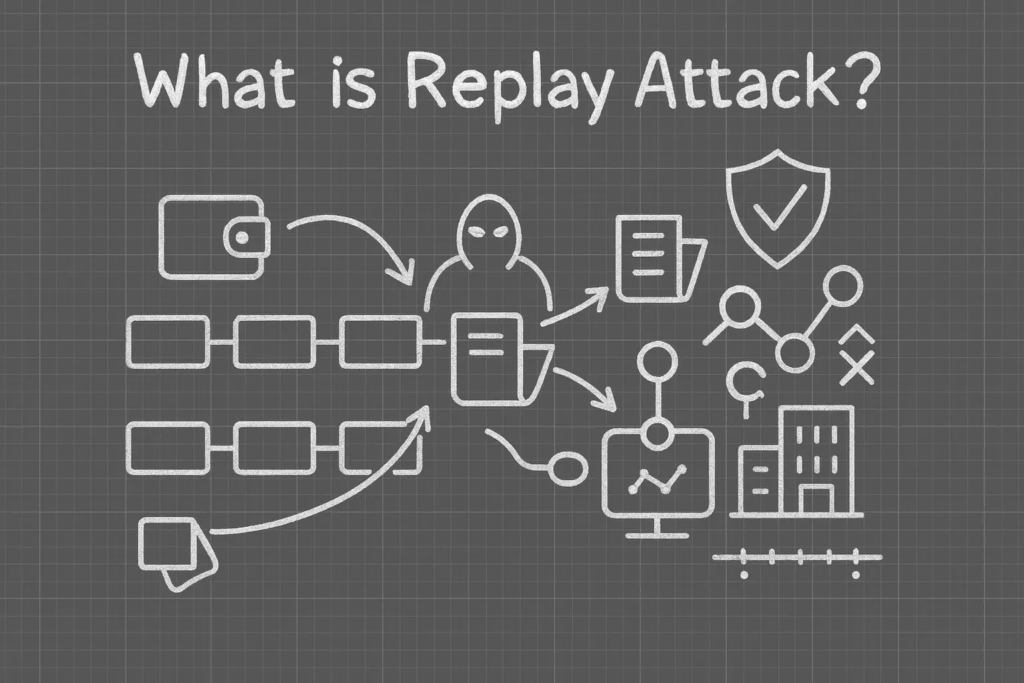
A replay attack is basically this:
An attacker records a legitimate request—like a login, form submission, or payment—and then sends it again. And again. And again.
No hacking skills required.
Just copy → paste → profit.
If your WordPress site doesn’t check whether a request has already been used, your site happily says:
“Sure! Let’s do that again.”
And that’s where the trouble starts.
Why WordPress Sites Are Prime Targets

WordPress isn’t insecure by default—but it is flexible. And flexibility invites mistakes.
Here’s why replay attacks love WordPress:
- Plugins aren’t always security geniuses
Some skip nonce checks. Some reuse tokens. Some just hope for the best. - Lots of sensitive requests flying around
Logins, checkouts, password resets, contact forms—you name it. - AJAX and REST APIs everywhere
Modern WordPress runs on background requests. Hackers love background requests. - SSL misconfigurations still exist
Yes, in 2025. Unfortunately.
What Replay Attacks Look Like in the Real World
Not theoretical. Very real.
Login Hijacking
A captured login request gets reused. Session hijacked. Someone else is “you” now.
Duplicate Payments
One checkout request → replayed → double (or triple) charges. Customers panic. You panic harder.
Form Spam on Steroids
One contact form submission replayed 500 times. Your inbox cries.
Abused API Endpoints
Unprotected AJAX or REST calls replayed until your server begs for mercy.
Bonus Level: HTTP/3 & 0-RTT Make This Trickier
Faster internet comes with… fun surprises.
TLS 1.3 introduced 0-RTT (early data), which is replayable by design. That’s not a bug—it’s physics.
If your WordPress site:
- Uses a CDN
- Supports HTTP/3
- Accepts early data without validation
Congratulations—you’ve widened the replay window.
If you don’t need early data, disable it. Speed gains aren’t worth security headaches.
How to Stop Replay Attacks on WordPress (Without Losing Sleep)
Good news: WordPress already gives you the tools. You just have to use them.
1. Use Nonces Like You Mean It
Nonces = “number used once.”
They’re WordPress’s built-in replay defense.
- Use
wp_nonce_field()in forms - Validate with
wp_verify_nonce() - Audit custom code and older plugins
If a request doesn’t have a valid nonce, it doesn’t get in. Simple.
2. Add Time Limits
Even good requests shouldn’t live forever.
- Add timestamps to requests
- Reject anything older than a few minutes
Replay window closed.
3. One-Time Tokens for Sensitive Actions
Password resets, magic links, payment confirmations—use once, expire fast.
Most serious plugins support this. Turn it on.
4. HTTPS Everywhere (No Exceptions)
HTTPS encrypts traffic, making replay capture much harder.
- Force SSL
- Fix mixed content warnings
- Stop pretending HTTP is “probably fine”
It’s not.
5. Lock Down AJAX & REST APIs
Never trust a request just because it “came from your site.”
- Require login states
- Validate nonces
- Check user permissions server-side
Every action should ask: Who are you, really?
6. Monitor Like a Paranoid Professional
You don’t need fear—you need visibility.
- Rate limiting
- Repeated request detection
- Security plugins with request logging
Replay attacks are repetitive by nature. That makes them detectable.
For Plugin Developers (Or Brave Custom Coders)
Extra credit if you:
- Check user roles, not just nonces
- Avoid caching dynamic forms
- Make payment logic idempotent (duplicates fail safely)
- Secure webhook signatures and timestamps
Future you will be grateful.
Final Takeaway: Replay Attacks Are Boring—but Dangerous
Replay attacks won’t make headlines.
But they will quietly:
- Drain money
- Spam systems
- Undermine trust
And WordPress sites that ignore them eventually learn the hard way.
Em AIRSANG, this kind of thinking is built into how we work.
We focus on cross-border websites, WordPress & Shopify design, and long-term platform stability—not just how a site looks on launch day.
If you’re building an international site, scaling eCommerce, follow AIRSANG.
Delivered Worldwide
AIRSANG delivers cost-effective website design, brand visual identity, and e-commerce solutions. From Shopify and WordPress to Amazon product images, we help global brands build, elevate, and grow their online business.
Conceber e construir um sítio Web WordPress ou um sítio empresarial com um sistema de comércio eletrónico completo para si.
Requisitos personalizados ou orçamentos especiais

Are 50 Plugins Too Many for a WordPress eCommerce Store?

Design da imagem principal para conversão de batom da Amazon

How Hackers Steal WordPress Admin Emails (And How to Stop Them)

O que faz uma base líquida da Amazon converter a imagem principal?

Como projetar uma imagem principal eficaz para cartuchos de filtro Amazon

Como duplicar páginas do WordPress sem danificar nada
Comparativo de cinco temas WordPress para animais de estimação
Comparando cinco temas de e-commerce de moda praia

Como desativar os comentários no WordPress (sem enlouquecer)